
Halo, kalau kamu merasa tulisan saya ngebantu kamu, kamu bisa ucapkan terima kasih lewat saweria .
If you feel this website help you, you can donate at saweria .
The Problem
When check using htop, fail2ban always the one who always appear who use all CPU on server
There is nothing wrong on server, no malware, only nginx installed.
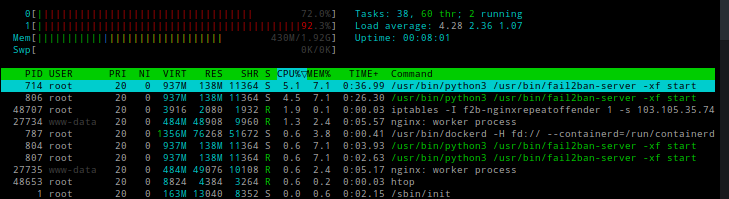
Fail2ban Eat All CPU
Analyze What’s Wrong With Fail2ban
The main problem was fail2ban log and nginx log (that monitoring by fail2ban)
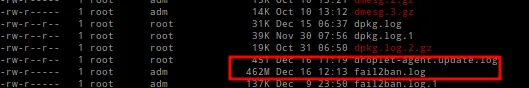
Big Log == Need More CPU To Read & Write
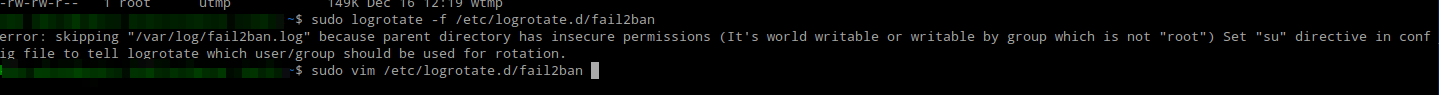
Error When Force Run Logrotate Fail2ban Log
Solution
Fix error logrotate fail2ban ’error: skipping “/var/log/fail2ban.log” because parent directory has insecure permissions (It’s world writable or writable by group which is not “root”) Set “su” directive in config file to tell logrotate which user/group should be used for rotation'
Open your fail2ban logrotate config
vim /etc/logrotate.d/fail2banAdd
su root admto make file owned by root and adm/var/log/fail2ban.log { #add this line su root adm weekly rotate 7 compress # Do not rotate if empty notifempty delaycompress missingok postrotate fail2ban-client flushlogs 1>/dev/null endscript # If fail2ban runs as non-root it still needs to have write access # to logfiles. # create 640 fail2ban adm create 640 root adm }Run
sudo logrotate -f /etc/logrotate.d/fail2ban
Fix your big nginx log file
Disable your access log
access_log off;Check your logrotate, if it not working do the same thing as fail2ban log tutorial above.
If you cannot disable it but it keep getting bigger, you create cron job to force logrotate to rotate your nginx log.
Check Other Log That Monitoring by Fail2ban
- Do the same thing, check logrotate file, if it doesn’t have logrotate config, create a new one.
Notes:
This case likely won’t appear on high end server
The biggest problem on this case was big log file
