
Halo, kalau kamu merasa tulisan saya ngebantu kamu, kamu bisa ucapkan terima kasih lewat saweria .
Hello, if you find this article helpful, you can express your gratitude through saweria .
What I Used in This Tutorial
I used Traefik setup from dockerswarm.rocks .
Docker v23.0.2
How To
Deploy whoami app, you can use
docker-compose up -dordocker stack deploy -c whoami.yml whoamiif you use swarm modeversion: '3.7' networks: whoami: external: false services: whoami: image: traefik/whoami:latest ports: - '8089:80' deploy: replicas: 4 update_config: parallelism: 2 order: start-first failure_action: rollback delay: 10s rollback_config: parallelism: 0 order: stop-first restart_policy: condition: any delay: 5s max_attempts: 3 window: 120s networks: - whoamiI Assume you use traefik.yml setup just like in dockerswarm.rocks
version: '3.3' services: traefik: image: traefik:v2.9.9 ports: # Listen on port 80, default for HTTP, necessary to redirect to HTTPS - 80:80 # Listen on port 443, default for HTTPS - 443:443 deploy: placement: constraints: # Make the traefik service run only on the node with this label # as the node with it has the volume for the certificates - node.labels.traefik-public.traefik-public-certificates == true labels: # Enable Traefik for this service, to make it available in the public network - traefik.enable=true # Use the traefik-public network (declared below) - traefik.docker.network=traefik-public # Use the custom label "traefik.constraint-label=traefik-public" # This public Traefik will only use services with this label # That way you can add other internal Traefik instances per stack if needed - traefik.constraint-label=traefik-public # admin-auth middleware with HTTP Basic auth # Using the environment variables USERNAME and HASHED_PASSWORD - traefik.http.middlewares.admin-auth.basicauth.users=${USERNAME?Variable not set}:${HASHED_PASSWORD?Variable not set} # https-redirect middleware to redirect HTTP to HTTPS # It can be re-used by other stacks in other Docker Compose files - traefik.http.middlewares.https-redirect.redirectscheme.scheme=https - traefik.http.middlewares.https-redirect.redirectscheme.permanent=true # traefik-http set up only to use the middleware to redirect to https # Uses the environment variable DOMAIN - traefik.http.routers.traefik-public-http.rule=Host(`${DOMAIN?Variable not set}`) - traefik.http.routers.traefik-public-http.entrypoints=http - traefik.http.routers.traefik-public-http.middlewares=https-redirect # traefik-https the actual router using HTTPS # Uses the environment variable DOMAIN - traefik.http.routers.traefik-public-https.rule=Host(`${DOMAIN?Variable not set}`) - traefik.http.routers.traefik-public-https.entrypoints=https - traefik.http.routers.traefik-public-https.tls=true # Use the special Traefik service api@internal with the web UI/Dashboard - traefik.http.routers.traefik-public-https.service=api@internal # Use the "le" (Let's Encrypt) resolver created below - traefik.http.routers.traefik-public-https.tls.certresolver=le # Enable HTTP Basic auth, using the middleware created above - traefik.http.routers.traefik-public-https.middlewares=admin-auth # Define the port inside of the Docker service to use - traefik.http.services.traefik-public.loadbalancer.server.port=8080 volumes: # Add Docker as a mounted volume, so that Traefik can read the labels of other services - /var/run/docker.sock:/var/run/docker.sock:ro # Mount the volume to store the certificates - traefik-public-certificates:/certificates command: # Enable Docker in Traefik, so that it reads labels from Docker services - --providers.docker # Add a constraint to only use services with the label "traefik.constraint-label=traefik-public" - --providers.docker.constraints=Label(`traefik.constraint-label`, `traefik-public`) # Do not expose all Docker services, only the ones explicitly exposed - --providers.docker.exposedbydefault=false # Enable Docker Swarm mode - --providers.docker.swarmmode # Create an entrypoint "http" listening on port 80 - --entrypoints.http.address=:80 # Create an entrypoint "https" listening on port 443 - --entrypoints.https.address=:443 # Create the certificate resolver "le" for Let's Encrypt, uses the environment variable EMAIL - --certificatesresolvers.le.acme.email=${EMAIL?Variable not set} # Store the Let's Encrypt certificates in the mounted volume - --certificatesresolvers.le.acme.storage=/certificates/acme.json # Use the TLS Challenge for Let's Encrypt - --certificatesresolvers.le.acme.tlschallenge=true # Enable the access log, with HTTP requests - --accesslog # Enable the Traefik log, for configurations and errors - --log # Enable the Dashboard and API - --api networks: # Use the public network created to be shared between Traefik and # any other service that needs to be publicly available with HTTPS - traefik-public volumes: # Create a volume to store the certificates, there is a constraint to make sure # Traefik is always deployed to the same Docker node with the same volume containing # the HTTPS certificates - traefik-public-certificates: networks: # Use the previously created public network "traefik-public", shared with other # services that need to be publicly available via this Traefik traefik-public: external: trueAdd
--providers.file.filename=rules.ymlatcommandpartversion: '3.3' services: traefik: image: traefik:v2.9.9 ports: # Listen on port 80, default for HTTP, necessary to redirect to HTTPS - 80:80 # Listen on port 443, default for HTTPS - 443:443 deploy: placement: constraints: # Make the traefik service run only on the node with this label # as the node with it has the volume for the certificates - node.labels.traefik-public.traefik-public-certificates == true labels: # Enable Traefik for this service, to make it available in the public network - traefik.enable=true # Use the traefik-public network (declared below) - traefik.docker.network=traefik-public # Use the custom label "traefik.constraint-label=traefik-public" # This public Traefik will only use services with this label # That way you can add other internal Traefik instances per stack if needed - traefik.constraint-label=traefik-public # admin-auth middleware with HTTP Basic auth # Using the environment variables USERNAME and HASHED_PASSWORD - traefik.http.middlewares.admin-auth.basicauth.users=${USERNAME?Variable not set}:${HASHED_PASSWORD?Variable not set} # https-redirect middleware to redirect HTTP to HTTPS # It can be re-used by other stacks in other Docker Compose files - traefik.http.middlewares.https-redirect.redirectscheme.scheme=https - traefik.http.middlewares.https-redirect.redirectscheme.permanent=true # traefik-http set up only to use the middleware to redirect to https # Uses the environment variable DOMAIN - traefik.http.routers.traefik-public-http.rule=Host(`${DOMAIN?Variable not set}`) - traefik.http.routers.traefik-public-http.entrypoints=http - traefik.http.routers.traefik-public-http.middlewares=https-redirect # traefik-https the actual router using HTTPS # Uses the environment variable DOMAIN - traefik.http.routers.traefik-public-https.rule=Host(`${DOMAIN?Variable not set}`) - traefik.http.routers.traefik-public-https.entrypoints=https - traefik.http.routers.traefik-public-https.tls=true # Use the special Traefik service api@internal with the web UI/Dashboard - traefik.http.routers.traefik-public-https.service=api@internal # Use the "le" (Let's Encrypt) resolver created below - traefik.http.routers.traefik-public-https.tls.certresolver=le # Enable HTTP Basic auth, using the middleware created above - traefik.http.routers.traefik-public-https.middlewares=admin-auth # Define the port inside of the Docker service to use - traefik.http.services.traefik-public.loadbalancer.server.port=8080 volumes: # Add Docker as a mounted volume, so that Traefik can read the labels of other services - /var/run/docker.sock:/var/run/docker.sock:ro # Mount the volume to store the certificates - traefik-public-certificates:/certificates command: # Enable Docker in Traefik, so that it reads labels from Docker services - --providers.docker # new config - --providers.file.filename=rules.yml # Add a constraint to only use services with the label "traefik.constraint-label=traefik-public" - --providers.docker.constraints=Label(`traefik.constraint-label`, `traefik-public`) # Do not expose all Docker services, only the ones explicitly exposed - --providers.docker.exposedbydefault=false # Enable Docker Swarm mode - --providers.docker.swarmmode # Create an entrypoint "http" listening on port 80 - --entrypoints.http.address=:80 # Create an entrypoint "https" listening on port 443 - --entrypoints.https.address=:443 # Create the certificate resolver "le" for Let's Encrypt, uses the environment variable EMAIL - --certificatesresolvers.le.acme.email=${EMAIL?Variable not set} # Store the Let's Encrypt certificates in the mounted volume - --certificatesresolvers.le.acme.storage=/certificates/acme.json # Use the TLS Challenge for Let's Encrypt - --certificatesresolvers.le.acme.tlschallenge=true # Enable the access log, with HTTP requests - --accesslog # Enable the Traefik log, for configurations and errors - --log # Enable the Dashboard and API - --api networks: # Use the public network created to be shared between Traefik and # any other service that needs to be publicly available with HTTPS - traefik-public volumes: # Create a volume to store the certificates, there is a constraint to make sure # Traefik is always deployed to the same Docker node with the same volume containing # the HTTPS certificates - traefik-public-certificates: #mount rules to root (/) trafik image - ./rules.yml:/rules.yml networks: # Use the previously created public network "traefik-public", shared with other # services that need to be publicly available via this Traefik traefik-public: external: trueCreate new file
rules.yml, it will act like virtual block file in nginxhttp: routers: whoami-https: entryPoints: - https rule: "Host(`whoami.domainkamu.com`)" middlewares: # dont forget to add @docker because our traefik using docker - https-redirect@docker service: whoami tls: certResolver: "le" whoami-http: entryPoints: - http rule: "Host(`whoami.domainkamu.com`)" service: whoami services: whoami: loadBalancer: servers: - url: "http://192.168.1.2:8089" passHostHeader: trueRun
docker stack deploy -c traefik.yml traefik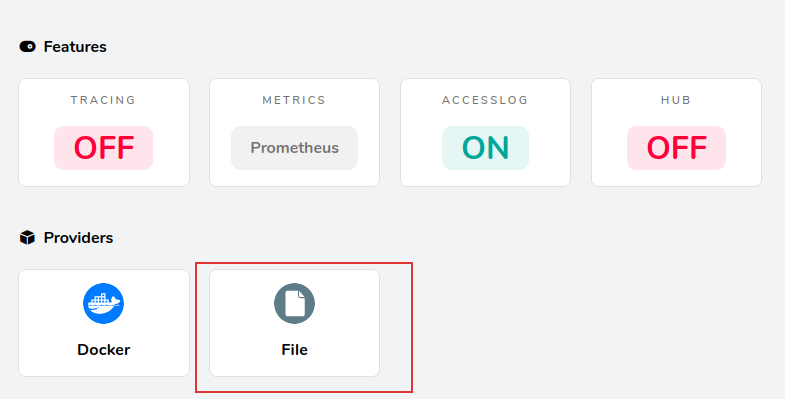
New Provider, File (rules.yml)
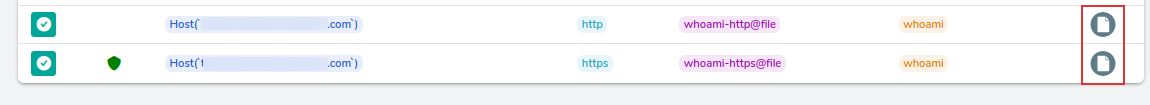
New Rule in HTTP Routers
